DFIR Playbook - Network Forensics
Introduction
This post aims to replicate my physical playbook on Networking and includes the following tools
- tshark
- capinfos
- Network Miner
- editcap
- nfdummp
- bro
- passivedns
- zcat
Future editions will include Snort and Live Monitoring
Contents
Converting PCAPs
| From | To | Command |
|---|---|---|
| pcap | netflow | nfcapd -r <pcapfile> -S 1 -z -l <Outputdirectory> |
| pcap | zeek | bro <profile> -r <pcapfile> profiles listed in /opt/bro/share/bro/site/<name>.bro |
| pcap | dns | passivedns -r <pcapfile> -l dnslog.txt -L nxdomain.txt Not included in SIFT, see repo |
| pcapng | pcap | tcpdump -r <pcapngfile> -w pcap.pcap |
| gz | grep’able text | zcat <gzfile> |
| LargePCAP | FilteredPCAP | tcpdump port 80 -r in.pcap -w out.pcap |
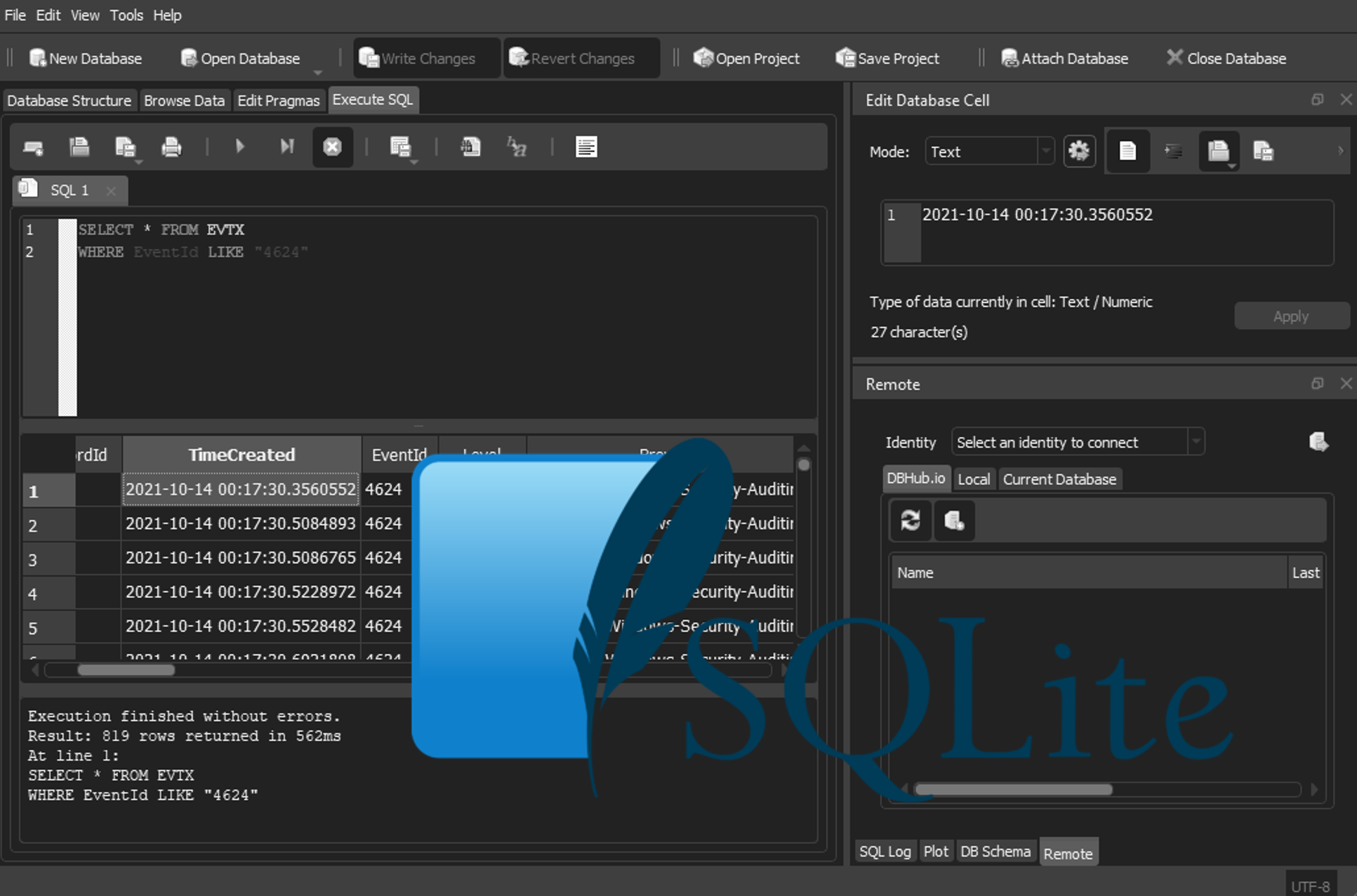
| LargePCAP | PlainTextWebPCAP | tshark -r Capture.pcap -Y "http.request or http.response or dns" -w Capture-Web.pcap Note:tshark will ONLY capture port 80, if HTTP traffic is on other ports, use TCPDump with port numbers |
Analysing PCAPs
| Description | Command | |
|---|---|---|
| HTTP Packet Counter | tshark -r <pcapfile> -z http,tree -q |
|
| Info | capinfos <pcapfile> |
|
| Basic filter output | tshark -r <pcapfile> -Y '<filters>' See Wireshark wiki or Unit42 for filter examples Note:tshark uses wireshark filters |
|
| Get files from pcap | tcpflow -r <pcapfile> -o <outputdirectory> or networkminer *Note: see Netresec for network miner installation instructions |
|
| Splice PCAP by before time | editcap -B "<YYYY-MM-DD HH:MM:SS Before Time>" <pcapfile> spliced.pcap |
|
| Splice PCAP by after time | editcap -A "<YYYY-MM-DD HH:MM:SS After Time>" <pcapfile> spliced.pcap |
|
| Forensics Analysis | tshark -r <pcap file> -Y <display filters> -T fields -e <Fields To display> Can be combined with |sort|uniq -c | sort -nr for statistical analysis Fields Use one -e for each field, examples include ip.addr udp frame.number or to show protocol fields from wireshark use _ws.col for example _ws.col.info or _ws.col.dns.query. To print all available fields use tshark -G fields or see Wireshark documentation |
|
| Filter pcaps (Reduce them down) | tcpdump -n -r <pcapfile> -w out.pcap <filter> filter could be udp and port 53 for DNS traffic see TCP Dump filters for more examples |
|
| Yet Another Filter pcaps (Reduce them down) | .\tshark.exe -r <input pcap> -Y <display filters> -w out.pcap |
|
| Dump netflow | nfdump -R <inputdirectory> <options> <filter> -o fmt.<format string> see 572 Poster for usage |
|
| Convert PCAP to http.log, files.log, conn.log Not nativley included in SIFT, download from zeek-packages |
zeek -r <filename> |
|
| Filter zeek columns | cat http.log | zeek-cut column_name |
|
| DNS Quick Wins | tshark -r <pcap file> -z dns,tree |
grep |
Extracting Certificates for TLS Traffic
- Open Wireshark
- Find the relevant certificate with the following wireshark filter
tls.handshake.type == 11and an identifier such as IP or domain name that resolves to that endpoint. You can also usetls.handshake.extensions_server_name contains <name>if you know the domain name then follow the stream. - Right click the certificate entry and selct “Export Packet Bytes”

- Save the file as a .der certificate
- Convert to pem with openssl x509 -inform der -in hotjar.der -out hotjar.pem
Netflow
- WIP
Snort
- WIP